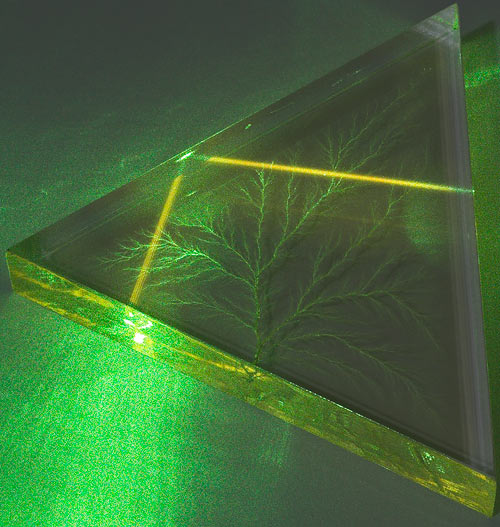
The other day I was shining a dangerously bright green laser through a Lichtenberg figure, as I'm sure all of you have done from time to time, and I discovered something interesting.
What?
Oh, all right. I'll explain.
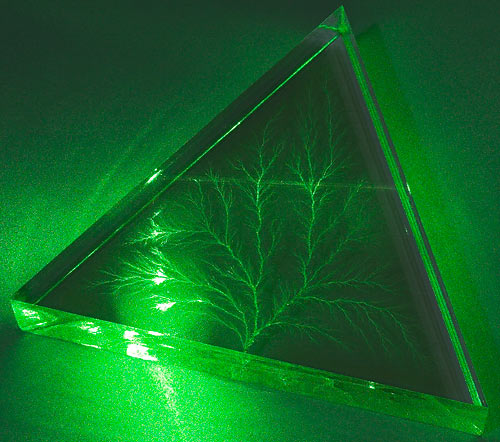
This is a Lichtenberg figure.
Well, technically, the Lichtenberg figure is the feathery ferny shape inside the block of clear acrylic. The shape is a void burned into the plastic by a powerful electric discharge.
A Lichtenberg figure is, in brief, the shape of an electrical discharge. Specifically, it's the shape of an electrical discharge from an area to a point - sometimes over time, but usually all at once.
The acrylic-block type of Lichtenberg ornament is definitely of the all-at-once variety. To make one, you have to shoot your acrylic with a fairly high powered electron beam, also known as a cathode ray.
The electron beam in a Cathode Ray Tube (CRT) television or computer monitor - which, yes, actually is a kind of particle accelerator - delivers electrons with maybe 20,000 or 25,000 electron volts (20 to 25keV) of energy.
That's quite enough to produce considerable X-ray radiation when the electrons strike the inside of the tube - which is why CRTs are made from leaded, radiation-blocking glass - but it's only 1%, at best, of the energy you need to drive electrons even a centimetre or so into a plastic target.
If your electron beam is powerful enough to do that, several seconds of exposure will cause the plastic to acquire a absolutely terrific level of charge. Up in the low megavolts, and with total stored energy ranging from that of a tiny to that of a quite large pistol cartridge.
Then you bring an earthed contact close to one side of the block.
And bang, there's your Lichtenberg figure.
It's been speculated that the feathery tips of the figure are present all the way down to the molecular level.
The world's premiere - actually, pretty close to the world's only - supplier of Lichtenberg figures burned into clear acrylic blocks is Bert Hickman's Stoneridge Engineering. That's one of Bert's in the video above, and I've bought a total of three smaller figures from him over the years, from his eBay store here. This equilateral triangle figure is four inches on a side, and cost me $US24.95 plus postage.
As acrylic Lichtenberg figures get bigger, the energy needed to make them rises, and is soon well beyond what your common-or-garden medical LINAC can manage. This sort of accelerator is not something you can make at home; it's very difficult to get even 1MeV out of a homebuilt unit, even if you're the kind of kid who is only bullied by the members of the football team who didn't know about all the jocks at your old school whose hair and teeth fell out before they died.
You need something like one of the big blighters used to irradiate food. This is why Bert's real monsters are rather expensive.
When high energy electrons hit acrylic, they don't just settle peacefully into the polymer matrix. They actually hit hard enough to discolour the plastic on the side on which the beam enters. This effect is known as "solarisation", because it looks not unlike the discolouration caused by long exposure to ultraviolet radiation (which only has energy of about ten electron-volts).
The electrons actually end up charging the plastic a bit beyond the discoloured deceleration zone. So if you look at an acrylic Lichtenberg figure from the side...
...you can quite clearly see the discoloration and the Lichtenberg figure itself as separate layers.
The solarisation nestles around the Lichtenberg figure like a little bathtub. It fades out around the edges, but those edges rise up around the lightning-shape on all sides.
And this is what I noticed when I was fooling around with my laser.
Shining the laser through the un-solarised part of the figure...
...produced pretty much the effect you'd expect.
But shining it through the solarised portion...
...gave a, much brighter, amber diffusion glow. You can see the beam turning amber as it hits the solarised portion of the plastic.
There's no great mystery about why the beam looks brighter in the solarised area. That seems to simply be because it's travelling through damaged polymer that scatters more of the light.
But the distinct amber colour was a surprise.
Only the scattered light is amber; the main beam's the same colour coming out of the block as it was going in.
Here's the unsolarised side, again.
Another interesting thing about solarisation is that it heals. Over a few years, if you don't expose the acrylic to any more high-energy insults, the orange tint goes away.
The first Lichtenberg figure I bought from Bert was a little two-incher, which I purchased back in 2004. I can't remember whether it had visible solarisation when I got it, but it doesn't now - and a green laser beam stays green all the way through it.
UPDATE: Find some high-res video of acrylic Lichtenberg figures being made in this post!