Suddenly, I've got a few readers - who are presumably, as is usually the case, representative of a lot more people - complaining about "fake antivirus" malware pop-ups when they visit dansdata.com.
Some people will see crapware pop-ups when they visit any random site, because they installed some crapware in the past, and now it's wedging itself into their browser all the time, showing them porno ads or asking them to install more crapware. (Or it may just be quietly waiting for them to type some interesting-looking usernames and passwords.)
This is not like that. This really does seem to be some actual malware associated directly with dansdata.com.
The only reader who managed to see what the bad ad did in any detail reported that it:
1: Apparently opened a PDF file in the Internet Explorer Adobe Reader plug-in
2: Used some exploit in that to install crapware called "Antivirus Live"
3: Popped up tons of fake system errors and immediately made his life very miserable
Another reader didn't see what the heck actually happened, but swears he never clicked an "OK, install whatever the hell it is you want to install!" button, also received a delicious heaping mouthful of brown and steaming fake antivirus software.
Yet another reader also had the experience that's more normal among drive-by banner-ad crapware-installer victims, which is to say:
1: Reader is peacefully reading one of my pages.
2: Reader clicks on a link to another of my pages.
3: Reader suddenly gets a bunch of terrifying popups about viruses.
4: Reader employs the sure-fire highly technical hacker-neutralisation technique.
5: Reader comes back to computer later, and spends hours on end trying to remove all of the malware that installed itself entirely without reader's knowledge. This can be a huge pain.
(Note that that post is three years out of date, and about me dealing with a really mild crapware problem. I presume that current crapware swims up your urethra and then flicks out a crown of asbestos thorns.)
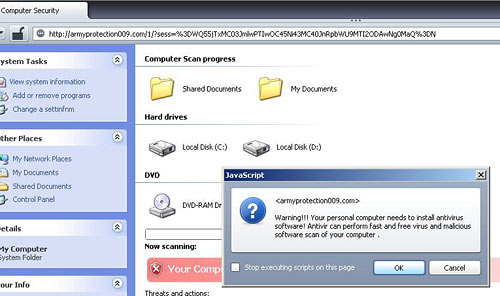
Another reader reported that the bad ad, or whatever the heck it is, tried to redirect to armyprotection009.com, which is on Firefox's "Attack Site" list (and also Chrome's, and I presume recent versions of various other browsers too).
That site's purpose in life...
...seems to be to pretend to be a Windows folder with a scary security warning in it, and get you to click OK to install "Antivir", which may or may not be the same BS malware antivirus as the apparently-installed-via-PDF "Antivirus Live" above.
I don't know for sure what it is, though, because armyprotection009.com is as I write this not resolving to anything any more. (I presume this is another of those weird hosting deals where sites, and the very nameservers that resolve them, come and go like the unlocatable voices of invisible summer insects. It's all very poetic.)
Even if I can find one of the redirected-to sites, that doesn't help much, because I need to know where the nasty redirecting ads are coming from. I presume it's either some exploit on the actual Web server, or an ad being served by one of the two outfits that serve ads to dansdata.com, Burst and Google.
(There are other ads on the site, most notably all the click-here-to-buy ones from Aus PC Market, but they're just a static image and link, not something all rich-media-y being served from somewhere far away.)
I know Burst have "subcontractors" who run ads not entirely under Burst's control; that's caused some scammy ads to show up from time to time, but never any actual malware. I don't know whether Google does a similar subcontracting thing. And it's made even harder to figure out by the way these crap-ads works. You see, like legitimate advertisers who try to avoid advertising the new season's Buicks to people who live in Sweden, crapware-servers serve different things to different IP addresses.
So even if it's a Burst subcontractor - not that I'm saying that it is - that's serving the ad entirely deliberately and not because some server of theirs has been compromised, it's perfectly possible that even if Burst carefully screen every single thing served in their name, they'll never see the malware, because the malware authors have Burst's whole IP range on a "do not serve malware to" list.
(This may fall down when a Burst employee goes home and uses his home ADSL connection to look at some site that runs his company's ads, of course.)
So now I'm e-mailing Burst and Google and my Web hosts. And with any luck, this post will crowdsource some more info.
I know there are people reading this who have a computer full of sacrificial virtual machines, and/or serious TCP/IP-and-Web chops. If any of you would like to dangle an unsuspecting virtual PC's Internet Explorer 6 in front of dansdata.com for a few force-refreshes, or (more importantly) trace where the hell this shit is actually coming from, then please, please do.
8 December 2009 at 1:26 am
I love Firefox and Prefbar, it makes it so darn easy to surf with JavaScript turned off!
8 December 2009 at 1:32 am
I had it come up twice and killed it before it did anything.
I wasn't able to replicate it on a test machine so thought it may have been my end, but kaspersky and super"califragilisticexpi"anti spyware found no problems.
On the same day I had another odd, unrepeatable problem with http://www.reallifecomics.com/ resolving to google.com even inheriting the google favicon which remains now.
not sure if there related but it's rare for me to get 1 problem let alone 2 in 1 day.
I saw it running chrome, can't replicate in any other browser or OS now.
Most likey a "drive by" ad infection..
8 December 2009 at 1:37 am
I have had hack attempts from very mainstream sites, probably from some hacked ad on the page. The bad guys shop probably around to find vendow with their guard down.
8 December 2009 at 2:42 am
It's surprising that you allowed this to happen, considering your technical knowledge. What caused this to occur?
8 December 2009 at 3:16 am
That's... kind of what I'm trying to find out :-).
I don't administer the dansdata.com server, or audit the ads that get served on the site. If you're a site owner and this happens, there really is no way for you to find out how it came to pass, without asking the server admins and ad companies.
(Which I've done. Google's ask-us-a-question interface is strongly reminiscent of a Choose Your Own Adventure book; you keep paging back after finding your choices have killed your chance to send an actual inquiry... and then you discover that the book actually doesn't let you do what you really want to do at all. I ended up submitting a query about suspicious clicks on ads, which was not at all the title of the thing I clicked on to get there.)
I can block ads for particular sites for the Google ads, and I can block categories of ads and also individual ads to quite a fine level of granularity with Burst. But if some advertiser is not acting in good faith, or is serving ads from a compromised server, there is as yet no way to quickly and automatically shut that advertiser off, without just not running ads at all any more.
(Deem usual Slashdot-commenter rant about using IE and running as root and Windows vs Linux and so forth to have been included here. Someone running Windows from a limited account who still has the ability to install applications can probably also still install malware from malicious pop-ups, though.)
8 December 2009 at 5:34 am
Maybe it's the langoliers, you haven't updated in a month.
but seriously, perhaps you should just shut off all the adds and see if the problem goes away, that way you rule out your host, then just trying turning the google ads back on etc.
Also I assume you can check your server's apache, php, perl versions etc and check for known exploits make sure they're patched (even if you couldn't fix it yourself you can check).
I don't see anything but i'm running FF 3.5x with adblock.
8 December 2009 at 6:13 am
I pulled up http://www.dansdata.com in an IE6 browser within a VM. I visited four pages on the site, received two popup ads for car insurance, and had a streaming video start in one of the ads pulling down about 3MB of video. I didn't once see a "scary computer warning" or any other attempt to install malware on the machine.
During this time, the machine communicated with:
138.108.23.100 for tracking purposes
206.57.28.50 for tracking purposes
207.46.148.32 for ads
208.71.122.60 for ads
209.50.189.199 for tracking purposes
209.8.118.112 for ads
209.8.118.130 for ads
209.8.118.137 for ads
209.8.118.40 for tracking purposes
209.8.118.66 for ads
208.8.118.89 for video
209.8.118.90 for ads
218.185.51.82 for ads
63.208.235.31 for ads
63.208.235.96 for ads
64.208.187.123 for tracking purposes
64.233.169.148 for tracking purposes
64.236.144.229 for ads
64.4.241.33 for encrypted data (paypal)
64.85.21.19 for the site data
64.85.9.37 for ads
64.94.107.14 for tracking
65.164.242.200 for tracking
64.164.242.247 for ads
64.55.87.80 for ads
65.60.42.202 for tracking
68.142.123.254 for ads
72.20.120.224 for ads
72.21.81.133 for ads
72.233.86.254 for ads
74.125.91.149 for ads
74.125.91.157 for ads
74.125.91.166 for ads
76.13.18.77 for tracking
I didn't see anything too nefarious in there, but damn, that's a lot of ad and tracking traffic for pulling up three web pages.
YMMV,
Eric
8 December 2009 at 8:19 am
Just to point out @#1, even with JS totally disabled, whether or not you have addons to facilitate doing that without making the 'net totally unusable... if the malware is in fact spread through a hole in *Adobe Reader* (or more specifically the plugin which embeds it in you browser), JS doesn't even enter into the equation. The problem with malware nowadays is that the old line conventional wisdom (don't run EXEs from email or the Internet without virus scanning them first, don't click on links if you don't know/trust the site they point to, etc) isn't enough anymore. As Dan points out, you could visit a site you know and trust (dansdata.com, for example), click no confirmation boxes, download / run no binaries, even be away from the computer entirely, and be infected simply by a combination of compromised 3rd-party content (like ads) and a browser or browser-plugin vulnerability. Frankly it's really scary stuff.
8 December 2009 at 8:36 am
Burst have gotten back to me with an ad that they think may be related to the problem. I've disabled that ad, and another one that looked a bit like it.
Isn't it bizarre that the current state of the malware-scumbags-vs-normal-people chess game is that the normal people, even the ones whose business it is to serve the ads that the scumbags subvert, only seem to be able to suspect where the problem may be!
8 December 2009 at 9:22 am
Hey Dan,
Check with Agg, Ocau seemed to start crashing with a similar issue. It is still down....
He **may** have some further clues for you.
8 December 2009 at 11:14 am
I'm now pretty sure there's nothing wrong with the actual server. SecureWebs didn't notice anything wrong with it before I mentioned this problem to them, and they've now run a couple of different scanners over it with no result. It really looks like a subverted ad. (Which may now be banished from the site, because I've disabled the ad that Burst were suspicious about.)
8 December 2009 at 11:25 am
I noticed this problem the other day - but it only happened to me in a version of Chrome I happened to be using, with no ad blocking. Firefox, with which I use Adblock Plus, had no problems. I believe ABP prevents the ad content from even being downloaded, rather than just hiding it (?), which seems to lend support to the dodgy-ad theory.
8 December 2009 at 2:22 pm
What banners did you disable on Burst? I have the same problem on my website and I also run Burst (and Tribal Fusion) ads. thx
8 December 2009 at 3:00 pm
*sigh*
Crime is getting so...impersonal...these days. Whatever happened to the hardworking honest thief who was polite about ripping you off?
8 December 2009 at 4:43 pm
I'm far from sure that this is the correct, or the only, culprit, but Burst told me to disable "PerfectMatch DR Int $1.20CPM". There was another "PerfectMatch" ad in rotation too, so I disabled that as well on general principles.
Burst's support seems to be pretty good on this, as far as it goes. (Not a peep out of Google yet, natch.) But just "being able to tell your customers what ad probably installed a virus on a thousand of their readers' computers, so they can turn that ad off" is, of course, not exactly an air-tight solution to the problem.
I asked the Burst support organism what Burst is doing to prevent ad subversion from happening in the first place, but have not yet received a reply.
8 December 2009 at 6:00 pm
@Coderer: next step in keeping Iffy Stuff at bay in attacks like described, is having a well-stocked hostsfile (and/or local DNS) serving all requests for addresses of Iffy Hosts (or entire Iffy Domains) with a stern 0.0.0.0. That won't stop malware that has hardcoded IP addresses in it, but malware pushers like to be flexible in where they host their stuff, and hardcoded IP addresses are very much less so than hostnames. Next step after that is having the firewall dropping all packets to and from original addresses associated with these domains (or at least the more pesky ones) on the floor too, but so far I haven't seen any great need to spend my Round Tuits on that bit.
You'll find one at http://hostsfile.mine.nu/
8 December 2009 at 6:29 pm
When I was updating my own hosts file the other day (leaving OUT Burst and Google servers, specifically so I can have some day-to-day idea of what my site is showing to visitors), I used pgl.yoyo.org/adservers.
9 December 2009 at 3:45 pm
Not directly applicable to this problem, but I had one completely fuxxor my computer a couple of months ago that took me a damned week to figure out how they did it.
(Figure out how it happened, I mean. I just erased the drive and reinstalled to fix it.)
It was brilliant, and exceedingly evil.
I was searching for some obscure technical thing, like the options for a linux command or something. The first result in google seemed promising, its preview had the beginnings of the exact right answer. I clicked the link. Up pops the Internet Explorer/google "bad site, get me out of here" page. I blindly clicked the get me out of here button, and it happily returned me to google. Then I hear a sound playing- like an embedded flash annoyance module in a webpage. But nothing was open except google. Instantly, the computer freaks out and crapware starts flying everywhere. I pulled the plug and tried to fix it, but it was infested.
Turns out, that warning page was fake. When I clicked "get me out of here", I triggered the download. It made me crazy for a week until I could figure out how it got in there...
Good luck!
10 December 2009 at 1:08 am
Serves you right for besmirching wonderful companies like firepower.
10 December 2009 at 4:18 am
http://www.malwarebytes.org/
Pretty good if you are already infected!
10 December 2009 at 10:26 pm
I'm "the only reader" Dan mentioned :)
Since the attack, I've noticed a weird problem with IE that only seems to affect Google: when I start a new IE session and go to Google, the first few results start to load (but a LOT slower than usual) and are then suddenly redirected to one of several malware sites, one of which is http://www.malwarebytesa0.com or something like that (obviously a fake site)
If I manually type an address in, it's usually OK but sometimes redirects. I thought it may have been connected to Google ads, but even microsoft.com is redirecting occasionally. Other sites are completely fine though... I haven't found a pattern yet.
Anyway, it seems that although I've removed the main malware program itself, something is still active somewhere in my system :( I have disabled the Adobe Reader plugin, but it seems to be partially active still - I accidentally clicked a PDF link in IE and it still loaded the file in the IE window.
I installed Spybot Search & Destroy after the attack and it has picked up a change in IE security settings today - which I definitely didn't make myself! So it looks like it's not over yet... :(
I just had a thought, maybe the remaining bit of whatever awfulness is left in my system is triggered by pages containing certain ads? Not sure if that's possible though. I'll keep looking for more clues!
10 December 2009 at 10:31 pm
Oops, sorry about that, I didn't realise this page auto-links URLs. DON'T CLICK THAT LINK!!
10 December 2009 at 10:39 pm
I'm not sure whether you actually remembered it right or not, since there doesn't seem to be a server at that address at the moment. The domain is registered to someone, though, so I defused the link on general principles anyway :-).
11 December 2009 at 1:47 am
Thanks Dan. Yes, I probably got the address wrong, I was too busy trying to close the window before another fake-AV forced itself in :p
I checked the IE history and couldn't find anything
I installed Anti-Malware from Malwarebytes, (thanks Oli!) which found a suspicious file in the IE cache and deleted it, and I also ran Hijackthis and found a registry entry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyServer = http=127.0.0.1:5555
I told HJT to fix it and IE seems to be working normally now.
However, the proxy address implies that the browser was being redirected by a program that's still on the system. None of the programs I've tried so far can find anything though...
11 December 2009 at 2:11 am
Sorry, I shouldn't be typing while tired... "I checked the IE history and couldn't find anything" - I meant to delete that line.
What I was going to say was that I think the URL I typed may have been a component of the page, and not the URL of the page itself. I know roughly which page it was on, but I'm not going to load it again to find out!
I wish IE had more history detail and better sorting/search options in the history, including searching for page components, and I wish I could view the page source from History without loading the page again. That would make it a lot easier to trace all sorts of problems!
Does IE keep a full log of all files it downloads? My IE cache has been emptied since the initial attack, but there may be some evidence left somewhere...
11 December 2009 at 3:25 am
There seems to have been a few sites affected by ads recently. JB Hi-Fi and OCAU being two that I know of. Could be a trend?
http://www.securecomputing.net.au/News/161645,jb-hi-fi-overclockers-websites-compromised.aspx
11 December 2009 at 4:20 am
Though spybot is pretty good, it doesn't always pick up everything. You should try using the 'run on boot' (or whatever it's called) option. Also give adaware a try, which will also pick up a different subset of malware. AVG is also supposed to be good and has a free edition.
There was once another tool I used on my parents PC after it picked up some nasty malware. It was pay software, but there was a trial edition I used to remove the nasties. I can't remember the name, but I remember it was the only software that seemed capable of finding the actual problem (I realize how unhelpful that is :\ )
Sometimes though it (unfortunately) just seems to be easier to do a re-install then get rid of some of this crap...
11 December 2009 at 8:22 am
Malwarebytes' Anti-Malware - http://www.malwarebytes.org/mbam.php
Spybot Search and Destroy - http://www.safer-networking.org/en/download/
Lavasoft Adaware - http://www.lavasoft.com/products/ad_aware_free.php
This is my other most valuable tip for fixing broken TCP/IP stacks after cleaning particularly nasty items, I've probably stolen this text verbatim from some other site, apologies to whoever it was as I don't remember anymore:
A Windows XP machine can sometimes have its WINSOCK catalog become corrupted and it appears like a network connection is disabled. Well, this is not always the case. If you perform a
PING -a -n 1 127.0.0.1
Ping the loopback connection at the COMMAND prompt you will see this as the hostname reply:
pinging °ÿ with 32 bytes of data
That °ÿ is the telltale sign that the WINSOCK catalog is corrupted. Simply enter this command at a command prompt:
netsh winsock reset catalog
and reboot the machine. The problem will be cleared up.
Comment by Fallox — December 11, 2009 @ 8:21 am
11 December 2009 at 11:08 am
While we're all linking to stuff, here are a few more options:
Trend Micro's HouseCall
BitDefender Quick Scan (has a neat Firefox add-on)
Kaspersky Online Scanner (not available at the moment, but their free File Scanner is still up)
11 December 2009 at 1:25 pm
I just had a call from one of my computer customers, saying they had a "virus" I logged in remotely and saw it is the exact same one that hit your site.
But she had been at Amazon, a dialog had popped up warning of viruses and to "click ok" to remove them.
luckily she called me straight away and i killed it off and am now running a super-antispyware scan, but it looks clean still.
btw i have found super-antispyware finds and removes problems that spybot and adaware dont. took me a while to come around to super-anti as the name makes it sound like it IS spyware.
Also I use Kaspersky on my own pc's and AVG on my customers, call it job security. :D
14 December 2009 at 9:19 am
Hey Dan, get any more news on this one?
My customers husband seems to have clicked all over this thing and "installed" it...Its popping up every time they open IE now.
AVG sees it as a infected TEMP file but after scan and reboot it's still there.
They also mentioned seeing a "fake" google page..
14 December 2009 at 3:40 pm
Saw this at work on one of our employee's PCs. Luckily most of our users are limited only, but this fake anti-virus malware is actually pretty smart:
-Random folder creation under the user's profile folder a couple of levels deep and random file name executables there
-HKCU\Software\Microsoft\Windows\CurrentVersion\Run, a couple of executables listed there
-Inability logged in as user via Remote Assistance to run Task Manager or anything else useful (no command prompt either), simply multitudes of fake Windows warnings about virii infecting everything you're trying to run and asking you to run "scans"
-Simple solution of logging in as my admin account and flushing everything
-We run McAfee security software which didn't notice anything amiss even as craploads of popups masquerading as Windows popups polluted the user's Windows sessions.
I'll have to check the ticket I opened with McAfee and see where they are with updating their spyware definitions.